
November 8, 2021Fireside Chats
How to win in cybersecurity
Industry veteran and Forescout Chair Greg Clark weighs in on the challenges and opportunities in keeping enterprises safe
- The proliferation of network-connected devices has dramatically expanded the “attack surface” available to intruders, creating unprecedented cybersecurity challenges
- Enterprises must rethink the architecture of their networks to segment access and contain threats
- Cybersecurity remains fertile ground for building lasting enterprises, but it requires a sound strategy, relentless customer focus and collaborative culture
One of Greg Clark’s early experiences with cybersecurity dates back to his time at Bell Labs in the late 1980s, when he worked in a Faraday Cage, an enclosure designed to block magnetic fields, to protect his code from being stolen remotely by Russian intruders.
More than three decades later, many things have changed in the world of cybersecurity. Some have not. “The adversaries are still there, and there are lots of them,” Clark said. “What’s different is the methods change.”
Clark knows more about the topic than most. A veteran cybersecurity executive, he is now chairman of Forescout Technologies, a leading enterprise security company. In August 2020, Clark’s firm, Crosspoint Capital Partners, teamed up with Advent International to acquire Forescout. Before that, Clark was CEO of Symantec and of Blue Coat Systems, which Symantec acquired.
The biggest change in cybersecurity, Clark told Bryan Taylor, head of Advent’s technology practice, in a fireside chat, is that just about every device—from computers and phones to HVAC systems and door locks—is now online. This internet of things (IoT), or enterprise of things, Clark said, has dramatically increased the “attack surface” that’s vulnerable to intruders.
“There’s a case where a casino was hacked by a fish tank thermometer that was on the Wi-Fi,” he said. “Protecting that IoT attack surface is a big issue.”
Greg Clark
Chairman, Forescout Technologies, Managing Partner, Crosspoint Capital Partners
New challenges, new solutions
Cybersecurity, of course, has always been an arms race between attackers and defenders. For companies like Forescout—and its customers—staying ahead of potential intruders these days requires a new understanding of the myriad devices that touch their networks.
“Your end points and the data that you’re a custodian of is moving through this environment all the time,” Clark said. That forces CIOs and CISOs to focus on a new set of issues around platform integrity, especially as the speed of software development picks up. An active defense requires enterprises to focus on what Clark called “network admission” for new devices. “Where do I put this device? How do I classify this device?” he said. “How risky is it?”
Access and privileges should be determined based on the answers to these and other questions. “Which kind of network you put them on is extremely important,” he said. Segmentation and containment of potential problems, he added, have become critical “drivers for modern network construction.”
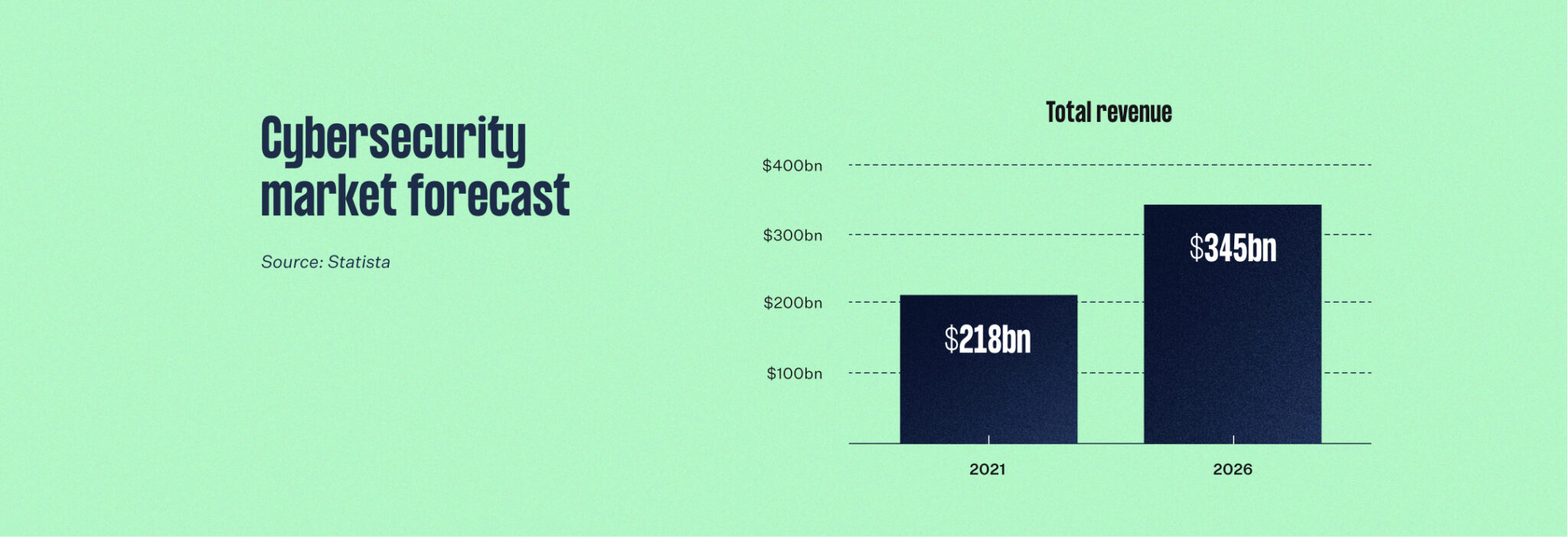
Combating threats big and small
While cybersecurity challenges are growing, new technologies are enabling cost-effective solutions that can scale. In particular, Clark said, cloud computing and AI techniques can be applied to detect abnormal behavior and stamp out potential intruders. “The power of machine learning or artificial intelligence is really being able to learn from a lot of historical data,” Clark said.
While companies are rightly focusing on fending off increasingly sophisticated attackers, Clark advised business leaders not to lose sight of the most common threats, which can be decidedly low-tech. “Often it’s a scam, it’s social engineering,” he said. “If you’ve got information that [someone] can steal and profit from, you will have serious adversaries trying to get it.”
Tips for building juggernauts
Perhaps because of its never-ending challenges, cybersecurity has been fertile ground for building lasting companies. Clark has done so again and again. He founded security software firm Dascom, which was acquired by IBM; led Mincom, which was acquired by ABB; grew Blue Coat Systems until it was acquired by Symantec; and continued that company’s growth. Clark offered insights for how to succeed at building juggernauts:
- Strategy really matters. How do you get a company to go from a few hundred million to over a billion dollars in revenue? How do you triple sales? “You have to have a good strategy for how you’re going to execute against the opportunity,” Clark said. And CEOs should focus on “really driving that strategy and focus deep into the corporation, deep into the management layers,” he added.
Greg Clark
- Seek insights from customers. Despite his vast experience, Clark says he continuously relies on customers for guidance. “I have never done anything without speaking to at least 80 big customers, medium-sized customers,” Clark said. Software vendors often make the mistake of showing up at a customer to tell them how to do things. “Try it the other way sometimes,” Clark said. Their opinions can be a powerful source of insights. “You talk to 15 of them and 10 of them tell you the same thing,” he said. “You should pay attention to that.”
- Culture and values are essential. “You can have a team of champions that loses and a team of well-qualified, well-trained players that absolutely crushes it because they behave as a team and support each other,” Clark said. “That comes from culture and a really good statement of values.” Driving that culture and values into the organization requires a determined effort at all levels of a company. “It’s not a one-time event,” he said. “It’s a continuous reinforcement process.”


